I coined the term “cryptic data” to mean information that isn’t easy to find or access by people who could make use of it. In one instance, cryptic data offers professional investors – portfolio managers and securities analysts – a source of proprietary information that can improve their ability to pick stocks and achieve superior performance relative to their benchmarks. Automation through
Having such technology comes at a time when active portfolio
Two factors have been driving the shift to passive investment management. One is the consistently poor performance of active managers relative to their relevant investment benchmarks, such as a major stock index. The second is that in a period of relatively low returns on investments, management fees have become more important, which favors the lower-cost passive alternative. Technology has made it feasible to create low-cost index fund alternatives to compete with active management.
Portfolio managers and securities analysts base their investment decisions for actively managed portfolios or investment recommendations on a variety of sources. Some of the most useful are based on personal relationships because they can provide more insight, context and nuance and because the information is not widely available. (I’m excluding insider information here.) However, a great deal of the research is based on generally accessible investment research and information services provided by trading platforms and information aggregators. These sources are an essential component of equity research, but because they are readily available, they offer limited competitive advantage to investment managers or research analysts. Cryptic data, on the other hand, can provide investors with an edge in stock selection because it requires individual insight to understand what information is necessary, where it is located and why it is useful, as well as the analytic skills to understand what it means.
Cryptic data can be found on any industry or subject somewhere in the Internet. Here are a few examples:
- Tables of related data assembled through repetitive queries of a free or paid data source (such as patents, real estate ownership or uniform commercial code filings)
- Store or retail outlet locations
- Product lines or price lists
- Industry data collected by a group that makes it available only to members
- Data contained in footnotes in financial filings that are not already collected in tabular form by data aggregators.
Collected, aggregated and analyzed, cryptic data can provide companies and individuals with information and insight that is not readily available. This is particularly true of data sets gathered over time from a source or a combination of sources that can reveal trends and relationships that otherwise would be difficult to spot.
Collecting the data in a consistent format makes it easier to do mashups of data sets to understand trends or spot potential issues. For example, starting with a list of addresses of store locations of a retailer, restaurant chain or consumer services provider, it’s possible to assess their geographic dispersion to determine whether new locations will fill in gaps or on the other hand cannibalize sales at existing stores. The data also can underpin analysis of the amount of capital needed to add productive sites to increase market share in a region. Geographic areas of overlap with competitors can be assessed. Location-based demographic databases can provide insight into their proximity to target customers. The impact of weather or natural disasters on such chains can be pinpointed quickly. While this data is openly available, knowing what to look for, how to analyze it and how to assess the results requires individual insight, skill and experience. This proprietary element is what makes cryptic data valuable to active investment management. Until automation technology became available, collecting cryptic information was too time-consuming to be practical.
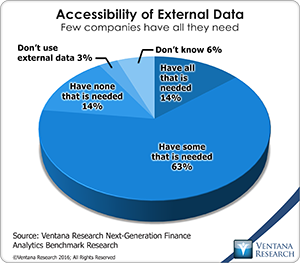 The challenge of accessing widely scattered information on the Web is daunting. Our next-generation finance analytics benchmark research shows that companies have limited access to information about markets, industries and economies. Only 14 percent of participants said they have access to all the external data they need. Most (63%) said they can access only some of it, and another 14 percent said they can’t access any such data.
The challenge of accessing widely scattered information on the Web is daunting. Our next-generation finance analytics benchmark research shows that companies have limited access to information about markets, industries and economies. Only 14 percent of participants said they have access to all the external data they need. Most (63%) said they can access only some of it, and another 14 percent said they can’t access any such data.
I recommend that portfolio managers and securities analysts consider how they might utilize cryptic data as part of their investment analysis. By automating the process of routinely collecting information and transforming it into usable formats, technology can expand the range of data available by lowering the cost of acquiring it. To address this constraint, data drones are designed for business users. They use a visual user interface design and hide some of the complexity inherent in the process. They can automate the process of collecting cryptic data and expand the scope and depth of data used for analysis, alerting and decision support. Having the ability to do this work in house can lower its cost in comparison to paying a service bureau. More importantly, by keeping the data retrieval and analysis in house (as opposed to contracting the work to a third party), the unique insights and the metrics that support it remain proprietary.
Automating the process of collecting cryptic data requires software that business people can use. I recommend taking a look at tools that can help you take advantage of cryptic data.
Regards,
Robert Kugel
Senior Vice President, Research

